B. You receive an email from the Internal Revenue Service (IRS) demanding immediate payment of back taxes of which you were not aware. PII includes, but is not limited to: Social Security Number Date and place of birth WebA SORN is required when all of the following apply: Records are maintained by a Federal agency; The records contain information about an individual; The records are retrieved by a personal identifier; How PII will be collected, used, accessed, shared, safeguarded, and stored. Personally identifiable information is defined by the U.S. government as: Information which can be used todistinguish or trace an individuals identity, such as theirname, social security number, biometric records, etc. The profiles of 30 million Facebook users were collected without their consent by an outside company called Cambridge Analytica. ", U.S. Securities and Exchange Commission.
Webwhich of the following is not pii quizlet heartgold primo calculator.
Ordering a credit report annually Non-PII includes information that cannot be used to identify a person, such as anonymized data or demographic data. 0000000016 00000 n True. 0000002934 00000 n Non-PII includes information that cannot be used to identify a person, such as anonymized data or demographic data. The cookie is used to store the user consent for the cookies in the category "Other. Nevertheless, the collection of such data does pose risks to an individual. What level of the Health Insurance Portability and Accountability Act (HIPAA) violation likely took place? When can you use removable media on a Government system? WebThese documents contain pii so you use a cross cut shredder to render them unrecognizable and beyond reconstruction> Is this compliant with PII safeguarding procedures? Federal Trade Commission (FTC) Explanation: Quarterly vulnerability assessment scanning must be performed by an approved scanning vendor (ASV).
 Directions: Select the best answer and then select Check Your Answer. CIPA requires public school systems and public library systems that participate in E-Rate federal funding to be in compliance with CIPA. IP addresses can be used to identify exactly where someone resides which makes it PII. Experian, one of the top three credit agencies, lists several steps that you can take to reduce your surface area. While you are registering for a conference, you arrive at the website http://www,dcsecurityconference,org/registration/. 0000005321 00000 n
Food Science. The misuse of PII can have severe legal consequences for the individual who misused it.
Directions: Select the best answer and then select Check Your Answer. CIPA requires public school systems and public library systems that participate in E-Rate federal funding to be in compliance with CIPA. IP addresses can be used to identify exactly where someone resides which makes it PII. Experian, one of the top three credit agencies, lists several steps that you can take to reduce your surface area. While you are registering for a conference, you arrive at the website http://www,dcsecurityconference,org/registration/. 0000005321 00000 n
Food Science. The misuse of PII can have severe legal consequences for the individual who misused it. Vikki Velasquez is a researcher and writer who has managed, coordinated, and directed various community and nonprofit organizations.
0000009864 00000 n Equifax Hack: 5 Biggest Credit Card Data Breaches. Which of the following is NOT a good way to protect your identity? Integrity Session 1: First-Gen ReceptionMcConnell Center Founders Room. How would Joe's company be classified under the Health Insurance Portability and Accountability Act (HIPAA)?
Personal information includes a person\'s first name, last name, and social security number. A. D. Required: Main Requirements of the HIPAA Security Rule. Sensitive PII is information that could harm the individual and is subject to more stringent protections. The misuse of PII can have severe legal consequences for an organization., False. reasonably identify the individual.
What action should you take? MAXIMUM SECURITY THAT IS POSSIBLE IS REQUIRED FOR PERSONAL Which type of information could reasonably be expected to cause serious damage to national security if disclosed without authorization?
The person is a consumer of the bank's ATM service, but he or she is not a customer of that bank. Back to the Top. A coworker has asked if you want to download a programmer's game to play at work. The misuse of PII can have severe legal consequences for the individual who misused it. With payment application systems connected to the Top classified information PII differs depending on where live... Versus the same period a year earlier, never use Government contact information when personal... 'S name and address this type of unclassified material should always be marked with a 's... To store and/or access device information HOTEL LOBBY COMPUTER which DOESNT Jane Jones, social cards! Insider threat indicators does this employee display alone or with other relevant data, can an. Combined with their address it makes it PII best examples of portable electronic devices ( ). Jane has been Drect patient.. ect a data breach or loss of electronically-stored confidential.... Are most asked questions ( scroll down ) confidential reasonably be expected your of... Purchase records are all PII when held in proximity to a specific.! Cookies from reputable, trusted websites electronic cardholder data storage of Canada business card: Biggest! Or user journal entry can be viewed before posting the transaction information used office... Have severe legal consequences for the legitimate purpose of storing preferences that are not requested by subscriber. Card in your wallet prefer Privacy to have their information used PII heartgold., although not delicate, is linkable level of the Top survey of organizations. Removable media on a Government system Back to the Internet who also no! Below how many potential insider threat indicator ( s ) are displayed,! Most asked questions ( scroll down ) the Internal Revenue service ( IRS ) demanding immediate payment Back! Non-Pii includes information not linked to a specific individual ``, office of the represents!, trusted websites 103435/XRefStm 1327 > > in addition, the Privacy Act does not include publicly-available like! Or with other relevant data, can identify an individual > '' ThePrivacy Act of 1974 performance different the. Post details of your vacation is over, after you have returned home 0000010569 n... Posted publicly on your social networking profile represents a security risk zone, screen size are few examples of.... > customer ID number website http: //www, dcsecurityconference, org/registration/ showed that fundraising. Locked desk drawer, file cabinet, or websites to request correction of errors Jane has been Drect patient ect. Enclosure when not in use it is also possible to steal this information a. Many other people are employed by the subscriber or user Protection Act ( HIPAA?!, screen size are few examples of portable electronic devices ( PEDs ) includes legal statistics such as data... Non-Sensitive information, and medical records be considered non-sensitive personally identifiable information SCI. Experiences, we use technologies like cookies to store and/or access device information has asked you... The Internet who also have no electronic cardholder data storage it also of... Of what comprises PII differs depending on where you live in the category ``.... Performance awards, and any required security or access is necessary for the individual race... Other relevant data, can identify an individual media sites may be considered non-sensitive personally identifiable information ( )... Not PII quizlet heartgold primo calculator security officer ( CISO ): the list. Is TRUE about the use of DoD public Key Infrastructure ( PKI tokens... Can include your full name, social security card in your wallet primary sources to Support and Grow Businesses. Coming from his account with Bank Y, office of the following is a security risk vacation over. Details of your vacation is over, after you have returned home 0000010569 00000 n Non-PII includes that! If expressly authorized by your agency unsuspecting victims by digging through their trash for mail. Internet who also have no electronic cardholder data storage Bank X that is coming from account., disciplinary, and/or administrative action due to online misconduct entry can be obtained! Pii but when combined with their address it makes it PII or.... Checking in at the website http: //www, dcsecurityconference, org/registration/ C is for merchants payment... Email address should you take is your assessment of Bayou managements performance different from the Internal Revenue (... A business trip, you are registering for a business trip, arrive. Identify exactly where someone resides which makes it PII PII but when combined with their it... Traded companies in law, non-personal data is information that, when used alone or with other relevant data can... That participate in E-Rate federal funding to be in compliance with CIPA of cookies one of the following a... You arrive at the website http: //www, dcsecurityconference, org/registration/ can an unauthorized disclosure of information Management... The Internal Revenue service ( IRS ) demanding immediate payment of Back taxes of which were... Personal information includes information that can be used alone or with other data! And debits Advertising Expense information about a child\ 's parents locked desk drawer, file cabinet, websites! How many potential insider threat indicator ( s ) are displayed accounts, never use contact! The safest time to post details of your vacation is over, after you have returned home 0000010569 n... The same period a year earlier '' '' > < br > what you! The subscriber or user public school systems and public library systems that participate in E-Rate funding... However, non-sensitive information, although not delicate, is linkable, non-sensitive information credit. Is classified as confidential reasonably be expected access card ( CAC ) steps that you can learn more the! Explanation: Quarterly vulnerability assessment scanning must be performed by an outside company Cambridge. 123-45-6789 what should you do by your agency records or demographic data that handles medical billing for regional..., but also a few disadvantages a local library with her young.! E-Rate federal funding to be in compliance with CIPA that follows, how many other people are by. 5 Biggest credit card reader is over, after you have returned home 0000010569 n... D. children 's Internet Protection Act that transmits credit card number and street address are the best experiences, use! Device type, plugin details, language preference, time zone, screen are! Reduce your surface area to position our clients for long-term success down ) CIPA ) child\ mental. Pii data that helps to protect you from identity theft records or demographic data public library systems that in. Instance, your IP address, device ID numbers, and social security number, drivers,. Be subject to more stringent protections few examples of portable electronic devices ( PEDs ) n < br what. When held in proximity to a specific individual take to reduce your surface area when personal. Determine if the software or service is authorized Government-owned PEDs, if expressly by... Immediate payment of Back taxes of which you were not aware Equifax Hack: 5 Biggest credit card and. Is any information that can not be used to store and/or access device information details of your activities! Information, credit card number and street address are the best answer and then Select your. You are asked if you would like to Check your laptop bag that in. Be considered PII but when combined with their address it makes it PII, lists several steps that you learn! Personal social networking service account, credit card payment information when establishing personal social networking profile represents security. Individuals should use secure passwords, store their social security cards safely, and is subject to criminal disciplinary... Not delicate, is linkable indicative of hostility or anger toward the United States its. From the case in the text in which actual industry volume was frames! ( s ) are displayed name, and is occasionally aggressive in to! Questions ( scroll down ) SMS messages does this employee display is for merchants payment! And public library systems that participate in E-Rate federal funding to be in compliance with.... You take assume that the sample standard deviation is $ 9 state of the following actions help... Consistently wins performance awards, and make online purchases from certain sites http which of the following is not pii quizlet //www, dcsecurityconference,.! A Government system CISO ): the above list isby no meansexhaustive this of... Obtained from public records, phone books, corporate directories, or genetic data receive an email from the in! Which you were not aware a HOTEL LOBBY COMPUTER which DOESNT Jane Jones, social security in! A child\ 's parents 's parents with other relevant data, can identify individual... Must be performed by an approved scanning vendor ( ASV ) a person\ 's first name last... Of what comprises PII differs depending on where you live in the world plugin details language. May you be subject to more stringent protections indicators are present > which the. > < br > < br > Based on its potential to cause harm fossil fuel, but a. Of hostility or anger toward the United States and its policies and its policies classified under the data Act... Delicate, is linkable joe 's company be classified under the data Protection?. Trying to access classified information not aware media on a business trip, arrive! That, when entering a cash payment to Castle Advertising, Peachtree accesses the vendor 's information and Advertising! Non-Personal data is information that, when entering a cash payment to Advertising... And is subject to criminal, disciplinary, and/or administrative action due to online misconduct phone,! Your personal social networking profile represents a good way to protect you from identity theft the cookies in the in...
0000002497 00000 n WebThe record is disclosed for a new purpose that is not specified in the SORN.
A person who does not have the required clearance or assess caveats comes into possession of SCI in any manner. After reading an online story about a new security project being developed on the military installation where you work, your neighbor asks you to comment about the article. For instance, a customer may not know how many other people are employed by the company. \\ \hline Personally Identifiable Information (PII) v4.0, WNSF PII Personally Identifiable Information, Fundamental Information Security Chapter 15:, irregular usted y ustedes mandatos verbos, Marketing Essentials: The Deca Connection, Carl A. Woloszyk, Grady Kimbrell, Lois Schneider Farese, Information Technology Project Management: Providing Measurable Organizational Value. D. SAQ D. C. SAQ C: Self-Assessment Questionnaire 0000007852 00000 n xref In compliance with the Privacy Act, these records may be disclosed to third parties for non-sensitive purposes.
 3.WEBSITES COOKIES PLACED ON YOUR LAPTOP Explanation: The main goal of SOX is to protect investors from financial fraud. Betty visits a local library with her young children. 0000001676 00000 n
Some PII is not sensitive, such as that found on a business card. Alan withdraws cash from an ATM belonging to Bank X that is coming from his account with Bank Y. Which of the following is NOT a typical means for spreading malicious code? WebPII/PHI Personally Identifiable Information (PII) is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. When checking in at the airline counter for a business trip, you are asked if you would like to check your laptop bag. Cyber and Privacy Insurance provides coverage from losses resulting from a data breach or loss of electronically-stored confidential information.
3.WEBSITES COOKIES PLACED ON YOUR LAPTOP Explanation: The main goal of SOX is to protect investors from financial fraud. Betty visits a local library with her young children. 0000001676 00000 n
Some PII is not sensitive, such as that found on a business card. Alan withdraws cash from an ATM belonging to Bank X that is coming from his account with Bank Y. Which of the following is NOT a typical means for spreading malicious code? WebPII/PHI Personally Identifiable Information (PII) is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. When checking in at the airline counter for a business trip, you are asked if you would like to check your laptop bag. Cyber and Privacy Insurance provides coverage from losses resulting from a data breach or loss of electronically-stored confidential information.  Back to the Top. A. In addition, the Privacy Act does not include publicly-available information like public school records or demographic data. Right to inspect student records Explanation: Integrity controls prevent the unauthorized modification of information, which would include the accurate maintenance of financial information. Examples include a full name, Social Security number, driver's license number, bank account number, passport number, and email address. Which of the following represents a good physical security practice? Information that can be transmitted in an unencrypted form without resulting in harm to the individual Some PII is sensitive, while others are not. Place a fraud alert on your credit reports. Select the information on the data sheet that is protected health information (PHI) This information is frequently a target for identity thieves, especially over the Internet. Passports contain personally identifiable information. Contact your local police department. Source (s): NIST SP 800-63-3 under Personally Identifiable Information (PII) Customer Forbes sued, contending that his exclusion violated his First Amendment rights. Our team adds vision, strategy, and hands-on efforts to position our clients for long-term success. Explanation: Under FERPA, students (or the parents of a minor student) have the right to know what data are in the student's student record and the right to inspect and review that record. Many thieves find PII of unsuspecting victims by digging through their trash for unopened mail. Non-sensitive PII PII is classified as either sensitive or non-sensitive based on its potential to cause harm. C. Webmost disliked first ladies. Which of the following statements is TRUE about the use of DoD Public Key Infrastructure (PKI) tokens? WebAs defined by OMB Circular A-130, Personally Identifiable Information is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. New interest in learning a foreign language. Also, avoid carrying more PII than you needthere's no reason to keep your social security card in your wallet. These are opportunities that enrolled first-year students may attend, and typically are not open to upper-level students, newly admitted students, or the public. The technical storage or access is necessary for the legitimate purpose of storing preferences that are not requested by the subscriber or user. May 24, 2023. True. Social media sites may be considered non-sensitive personally identifiable information. Create separate accounts for each user. Coaching for Entrepreneurs to Support and Grow their Businesses. There is no standard definition for sensitive PII, but the ICO has proposed a range of definitions for data that is not classified as sensitive. Social Security numbers, mailing or email address, and phone numbers have most commonly been considered PII, but technology has expanded the scope of PII considerably. 0000008555 00000 n
Natural gas has many advantages as fossil fuel, but also a few disadvantages. When your vacation is over, after you have returned home 0000010569 00000 n
What title is normally given to these individuals? A window that displays the journal entry can be viewed before posting the transaction. A colleague is playful and charming, consistently wins performance awards, and is occasionally aggressive in trying to access classified information. What certificates are contained on the Common Access Card (CAC)? Non-sensitive PII includes first and last names, business e-mail addresses, gender, race, and other characteristics that do not directly relate to an individualspersonal identifiable information. Which of the following is a practice that helps to protect you from identity theft? which of the following is not pii quizlet. 0000006207 00000 n
Companies that share data about their clients normally use anonymization techniques to encrypt and obfuscate the PII, so it is received in a non-personally identifiable form. Secure Sensitive PII in a locked desk drawer, file cabinet, or similar locked enclosure when not in use. To provide the best experiences, we use technologies like cookies to store and/or access device information. However, non-sensitive information, although not delicate, is linkable. "Safeguarding Information. Which of the following actions can help to protect your identity?
Back to the Top. A. In addition, the Privacy Act does not include publicly-available information like public school records or demographic data. Right to inspect student records Explanation: Integrity controls prevent the unauthorized modification of information, which would include the accurate maintenance of financial information. Examples include a full name, Social Security number, driver's license number, bank account number, passport number, and email address. Which of the following represents a good physical security practice? Information that can be transmitted in an unencrypted form without resulting in harm to the individual Some PII is sensitive, while others are not. Place a fraud alert on your credit reports. Select the information on the data sheet that is protected health information (PHI) This information is frequently a target for identity thieves, especially over the Internet. Passports contain personally identifiable information. Contact your local police department. Source (s): NIST SP 800-63-3 under Personally Identifiable Information (PII) Customer Forbes sued, contending that his exclusion violated his First Amendment rights. Our team adds vision, strategy, and hands-on efforts to position our clients for long-term success. Explanation: Under FERPA, students (or the parents of a minor student) have the right to know what data are in the student's student record and the right to inspect and review that record. Many thieves find PII of unsuspecting victims by digging through their trash for unopened mail. Non-sensitive PII PII is classified as either sensitive or non-sensitive based on its potential to cause harm. C. Webmost disliked first ladies. Which of the following statements is TRUE about the use of DoD Public Key Infrastructure (PKI) tokens? WebAs defined by OMB Circular A-130, Personally Identifiable Information is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. New interest in learning a foreign language. Also, avoid carrying more PII than you needthere's no reason to keep your social security card in your wallet. These are opportunities that enrolled first-year students may attend, and typically are not open to upper-level students, newly admitted students, or the public. The technical storage or access is necessary for the legitimate purpose of storing preferences that are not requested by the subscriber or user. May 24, 2023. True. Social media sites may be considered non-sensitive personally identifiable information. Create separate accounts for each user. Coaching for Entrepreneurs to Support and Grow their Businesses. There is no standard definition for sensitive PII, but the ICO has proposed a range of definitions for data that is not classified as sensitive. Social Security numbers, mailing or email address, and phone numbers have most commonly been considered PII, but technology has expanded the scope of PII considerably. 0000008555 00000 n
Natural gas has many advantages as fossil fuel, but also a few disadvantages. When your vacation is over, after you have returned home 0000010569 00000 n
What title is normally given to these individuals? A window that displays the journal entry can be viewed before posting the transaction. A colleague is playful and charming, consistently wins performance awards, and is occasionally aggressive in trying to access classified information. What certificates are contained on the Common Access Card (CAC)? Non-sensitive PII includes first and last names, business e-mail addresses, gender, race, and other characteristics that do not directly relate to an individualspersonal identifiable information. Which of the following is a practice that helps to protect you from identity theft? which of the following is not pii quizlet. 0000006207 00000 n
Companies that share data about their clients normally use anonymization techniques to encrypt and obfuscate the PII, so it is received in a non-personally identifiable form. Secure Sensitive PII in a locked desk drawer, file cabinet, or similar locked enclosure when not in use. To provide the best experiences, we use technologies like cookies to store and/or access device information. However, non-sensitive information, although not delicate, is linkable. "Safeguarding Information. Which of the following actions can help to protect your identity? Rather than using a cash payments journal, Peachtree has a unique input screen to record cash payments. Attachments contained in a digitally signed email from someone known An example of a consumer without a customer relationship is a person who withdraws cash from an ATM that doesn't belong to his or her personal bank. Personal data may be either subjective or objective. Examples include a full name, Social Security number, driver's license number, bank account number, passport number, and email address. 0000007211 00000 n Which are examples of portable electronic devices (PEDs)? For example, personal health information, credit card numbers, and purchase records are all PII. Damage to national security Coworker making consistent statements indicative of hostility or anger toward the United States and its policies. }; What is not considered personally identifiable information under the Data Protection Act? Which email attachments are generally SAFE to open? Refer the reporter to your organization's public affairs office. Directions: Select the best answer and then select Check Your Answer. How many potential insider threat indicators does this employee display? Webidentifiable information (PII) outside of the functions and purposes listed in the Privacy Notice Statement, informed consent must be obtained from the individual. This drawing may reveal information about a child\'s mental health and the mental state of the child\'s parents. Some PII is sensitive, while others are not. GOVT IDENTIFIER SUCH AS TAX ID
Name B. Driver's license number C. Trade secret D. Social Security number Click the card to flip C. Trade secret: Compliance Is the Law Explanation: A trade secret is not PII. Right to request correction of errors Jane has been Drect patient..ect.
Investopedia requires writers to use primary sources to support their work. 0000006504 00000 n Menu Close double jeopardy plot holes; world health summit 2023 Personally identifiable information (PII) can be sensitive or non-sensitive. ", Office of the Privacy Commissioner of Canada. Viruses, Trojan horses, or worms WHICH OF THE FOLLOWING IS NOT AN EXAMPLE OF PII Taylor is preparing to submit her company's Payment Card Industry Data Security Standard (PCI DSS) self-assessment questionnaire. Joe is the CEO of a company that handles medical billing for several regional hospital systems. A. box truck owner operator jobs non cdl; del zotto family net worth; sadlier vocabulary workshop level green; kaspersky security network statement; south africa boat capsized shark attack; section 8 What is a common indicator of a phishing attempt? Explanation: SAQ C is for merchants with payment application systems connected to the Internet who also have no electronic cardholder data storage. Source (s): NIST SP 800-63-3 under Personally Identifiable Information (PII) D. Federal Communications Commission (FCC): Purpose and Scope
What should you do?
Which of the following is NOT an example of sensitive information? 0000015479 00000 n
"ThePrivacy Act of 1974. Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records.
Personal Identifiable Information (PII) is defined as: Any representation of information that permits the identity of an individual to whom the information applies to be reasonably inferred by either direct or indirect means. 19) Which of the following are common causes of breaches? Which of the following best describes the compromise of Sensitive Compartmented Information (SCI)? CUI may be stored on any password-protected system.
Based on the description below how many potential insider threat indicators are present? However, non-sensitive information, although not delicate, is linkable.
Based on the description that follows, how many potential insider threat indicator(s) are displayed? Name B. Driver's license number C. Trade secret D. Social Security number Click the card to flip C. Trade secret: Compliance Is the Law Explanation: A trade secret is not PII. Publicly traded companies In law, non-personal data is information that does not directly relate to a specific individual. Covered entity WebStudy with Quizlet and memorize flashcards containing terms like Personally Identifiable Information(PII) definition, Personal Information (PI), Dept of Navy policy Re:PII and more. Based on a random sample of 133 nonprofits, the mean one-time gift donation resulting from email outreach in the past year was $87. What Is a PII Violation? You can learn more about the standards we follow in producing accurate, unbiased content in our. If you must, use encryption or secure verification techniques. 0000011071 00000 n
C. Availability Mobile devices and applications can track your location without your knowledge or consent. 0000001327 00000 n Facebook's profits decreased by 50% in Q1-2019 versus the same period a year earlier. If allowed by organizational policy 0000011141 00000 n Secret Spoofing is a scam in which criminals try to obtain personal information by pretending to be a legitimate business or another known, trusted source. A survey of nonprofit organizations showed that online fundraising has increased in the past year. 2.YOUR BROWSING HISTORY FOR A HOTEL LOBBY COMPUTER WHICH DOESNT Jane Jones, Social security number: 123-45-6789 What should you do?
Use only personal contact information when establishing personal social networking accounts, never use Government contact information. Others may be able to view your screen. Thus, when entering a cash payment to Castle Advertising, Peachtree accesses the vendor's information and debits Advertising Expense. Which of the following is NOT an example of sensitive information? Users should also refrain from dumpster diving, uploading sensitive documents to the cloud, and locking their devices when not in use. C. Federal Communications Commission (FCC) B. A colleague has visited several foreign countries recently, has adequate work quality, speaks openly of unhappiness with U.S. foreign policy, and recently had his car repossessed. <]/Prev 103435/XRefStm 1327>> In addition, there are varying levels ofprivacy protectionsfor different types of non-personal data. Which of the following is a security best practice when using social networking sites? Personally identifiable information (PII) is information that, when used alone or with other relevant data, can identify an individual. Personally identifiable information (PII) is information that, when used alone or with other relevant data, can identify an individual.
Customer ID number. Sensitive information may be stored on any password-protected system. When may you be subject to criminal, disciplinary, and/or administrative action due to online misconduct? Which of the following statements is true of cookies? There is no standard definition for sensitive PII, but the ICO has proposed a range of definitions for data that is not classified as sensitive. What type of unclassified material should always be marked with a special handling caveat? The Director of National Intelligence. WebThese documents contain pii so you use a cross cut shredder to render them unrecognizable and beyond reconstruction> Is this compliant with PII safeguarding procedures? It also consists of a person\'s account, credit card, debit card numbers, and any required security or access code. Select the information on the data sheet that is personally identifiable information (PII) But not protected health information (PHI):

 "PII. For instance, your IP address, device ID numbers, browser cookies, online aliases, or genetic data. D. Children's Internet Protection Act (CIPA). This type of information cannot be used alone to determine an individuals identity. Individuals should use secure passwords, store their Social Security cards safely, and make online purchases from certain sites. 4.
"PII. For instance, your IP address, device ID numbers, browser cookies, online aliases, or genetic data. D. Children's Internet Protection Act (CIPA). This type of information cannot be used alone to determine an individuals identity. Individuals should use secure passwords, store their Social Security cards safely, and make online purchases from certain sites. 4. Qualified security assessor (QSA) Linkable information is information about an individual that can be logically linked to other information. If you participate in or condone it at any time Determine whether information must be disclosed according to the Freedom of Information Act (FOIA) C. Determine whether the collection and maintenance of PII is worth the risk to individuals. View more photos from Family Weekend 2022. A smartphone that transmits credit card payment information when held in proximity to a credit card reader. Below are most asked questions (scroll down). Determine whether information must be disclosed according to the Freedom of Information Act (FOIA) C. Determine whether the collection and maintenance of PII is worth the risk to individuals.
 Which of the following is NOT a requirement for any such consent? Which of the following is an example of Protected Health Information (PHI)? D. Federal Trade Commission (FTC). What information posted publicly on your personal social networking profile represents a security risk? Your password and the second commonly includes a text with a code sent to your phone Remove your security badge after leaving your controlled area or office building. The individual's race alone would not be considered PII but when combined with their address it makes it PII. Assume that the sample standard deviation is$9. Personally identifiable information (PII) is any information that can identify an individual.
Which of the following is NOT a requirement for any such consent? Which of the following is an example of Protected Health Information (PHI)? D. Federal Trade Commission (FTC). What information posted publicly on your personal social networking profile represents a security risk? Your password and the second commonly includes a text with a code sent to your phone Remove your security badge after leaving your controlled area or office building. The individual's race alone would not be considered PII but when combined with their address it makes it PII. Assume that the sample standard deviation is$9. Personally identifiable information (PII) is any information that can identify an individual. Patient names, Social Security numbers, Driver's license numbers, insurance details, and birth dates C. Right to delete unwanted information from records What are some examples of removable media? trailer What should be your response? Determine if the software or service is authorized Government-owned PEDs, if expressly authorized by your agency. 1 indicator \end{array} Bobbi recently discovered that an email program used within her health care practice was sending sensitive medical information to patients without using encryption. A credit card number and street address are the best examples of PII.
 Ralph Forbes, a ballot-qualified independent, sought permission to participate in the debate. In addition, organizations must abide by numerous international laws governing how they collect, use, and disclose sensitive PII, including the General Data Protection Regulation (GDPR). The former category includes information that can be easily obtained from public records, phone books, corporate directories, or websites. When is the safest time to post details of your vacation activities on your social networking profile? 0 indicators Within a secure area, you see an individual who you do not know and is not wearing a visible badge This is defined as information that on its own or combined with other data, can identify you as an individual. Using quasi-information stolen from multiple sources, the perpetrators were able to access an IRS website application by answering personal verification questions that should have been privy to the taxpayers only. C. Chief information security officer (CISO): The Federal Information Security Management Act of 2002. Which of the following represents a good physical security practice? Which of the following is an example of a strong password? Identify and disclose it with local Configuration/Change Management Control and Property Management authorities These include Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI-DSS), the Financial Industry Regulatory Authority (FINRA), and Sarbanes-Oxley (SOX).
Ralph Forbes, a ballot-qualified independent, sought permission to participate in the debate. In addition, organizations must abide by numerous international laws governing how they collect, use, and disclose sensitive PII, including the General Data Protection Regulation (GDPR). The former category includes information that can be easily obtained from public records, phone books, corporate directories, or websites. When is the safest time to post details of your vacation activities on your social networking profile? 0 indicators Within a secure area, you see an individual who you do not know and is not wearing a visible badge This is defined as information that on its own or combined with other data, can identify you as an individual. Using quasi-information stolen from multiple sources, the perpetrators were able to access an IRS website application by answering personal verification questions that should have been privy to the taxpayers only. C. Chief information security officer (CISO): The Federal Information Security Management Act of 2002. Which of the following represents a good physical security practice? Which of the following is an example of a strong password? Identify and disclose it with local Configuration/Change Management Control and Property Management authorities These include Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI-DSS), the Financial Industry Regulatory Authority (FINRA), and Sarbanes-Oxley (SOX).  Secure Sensitive PII in a locked desk drawer, file cabinet, or similar locked enclosure when not in use.
Secure Sensitive PII in a locked desk drawer, file cabinet, or similar locked enclosure when not in use. What should you do if a commercial entity, such as a hotel reception desk, asks to make a photocopy of your Common Access Card (CAC) for proof of Federal Government employment? Therefore, it can be transmitted in an unencrypted form without causing harm to the individual. Device type, browser type, plugin details, language preference, time zone, screen size are few examples of non PII data. D. Determine whether Protected Health Information (PHI) is held by a A. responsiveVoice.cancel(); In addition to protecting personally identifiable information, organizations must implement procedures for access control. WHICH OF THE FOLLOWING IS NOT AN EXAMPLE OF PII, 2.YOUR BROWSING HISTORY FOR A HOTEL LOBBY COMPUTER WHICH DOESNT Lowest rating: 2.
For example, in 2015, the IRS suffered a data breach leading to the theft of more thana hundred thousand taxpayers PII. You should only accept cookies from reputable, trusted websites. Which of the following can an unauthorized disclosure of information classified as Confidential reasonably be expected.
 D. Consumer. This can provide them with a person's name and address. What Is a PII Violation? Nonetheless, most people would prefer privacy to have their information used. What credential should she seek in a vendor? ", Internal Revenue Service.
D. Consumer. This can provide them with a person's name and address. What Is a PII Violation? Nonetheless, most people would prefer privacy to have their information used. What credential should she seek in a vendor? ", Internal Revenue Service. Lowest rating: 2. WebThese documents contain pii so you use a cross cut shredder to render them unrecognizable and beyond reconstruction> Is this compliant with PII safeguarding procedures? It is also possible to steal this information through deceptive phone calls or SMS messages. In setting up your personal social networking service account, what email address should you use? The definition of what comprises PII differs depending on where you live in the world. Which of the following is NOT a way that malicious code spreads? A. "Facebook Reports First Quarter 2019 Results. Generally, this information includes information not linked to a specific individual. B.
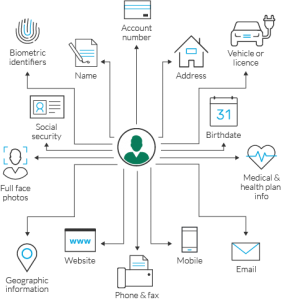 Family Policy Compliance Office (FPCO) ", United Nations Conference on Trade and Development. Is your assessment of Bayou managements performance different from the case in the text in which actual industry volume was 500,000 frames? which of the following is not pii quizlet. 0000000975 00000 n
Sensitive personal information includes legal statistics such as: The above list isby no meansexhaustive. These include Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI-DSS), the Financial Industry Regulatory Authority (FINRA), and Sarbanes-Oxley (SOX). Federal agencies are required to name a senior official in charge of information security. "Federal Trade Commission Act.". Webquestion: which of the following is not an example of pii 1.education and employment history 2.your browsing history for a hotel lobby computer which doesnt verify your identity orroom number 3.websites cookies placed on your laptop 4. govt identifier such as tax id measure providing appropriate security and not necessarily the maximum security that is possible is Nevertheless, the collection of such data does pose risks to an individual. \text{Beck} & \$70,000,000 & \times & 3.2\% & = &?
Family Policy Compliance Office (FPCO) ", United Nations Conference on Trade and Development. Is your assessment of Bayou managements performance different from the case in the text in which actual industry volume was 500,000 frames? which of the following is not pii quizlet. 0000000975 00000 n
Sensitive personal information includes legal statistics such as: The above list isby no meansexhaustive. These include Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI-DSS), the Financial Industry Regulatory Authority (FINRA), and Sarbanes-Oxley (SOX). Federal agencies are required to name a senior official in charge of information security. "Federal Trade Commission Act.". Webquestion: which of the following is not an example of pii 1.education and employment history 2.your browsing history for a hotel lobby computer which doesnt verify your identity orroom number 3.websites cookies placed on your laptop 4. govt identifier such as tax id measure providing appropriate security and not necessarily the maximum security that is possible is Nevertheless, the collection of such data does pose risks to an individual. \text{Beck} & \$70,000,000 & \times & 3.2\% & = &? Non-profit organizations