allintext username password
 To learn more about bcrypt, check out this excellent article: Hashing in Action Understanding bcrypt. His initial efforts were amplified by countless hours of community developed for use by penetration testers and vulnerability researchers.
To learn more about bcrypt, check out this excellent article: Hashing in Action Understanding bcrypt. His initial efforts were amplified by countless hours of community developed for use by penetration testers and vulnerability researchers. This browser does not support inline PDFs. Username and password authentication is a great starting point, but it's just not enough.
For example, you can apply a filter just to retrieve PDF files. Help for problems signing in. Want to learn more about Credential Stuffing Attacks? Downloads. dorking + tools. The Exploit Database is a Note there can be no space between the site: and the domain. menuentry 'Debian GNU/Linux' --class debian --class gnu-linux --class gnu --class os $menuentry_id_option 'gnulinux-simple-ea023db7-d096-4c89-b1ef-45d83927f34b' { While this does make it more difficult for a bad actor to exploit, it's still not impossible. You may be surprised at how fast a computer can brute force a seemingly complicated password. If you include [inurl:] in your query, Google will restrict the results to With its tremendous capability to crawl, it indexes data along the way, which also includes sensitive information like email addresses, login credentials, sensitive files, website vulnerabilities, and even financial information. Searching for LOG files will allow us to look for clues about what the credentials to the system or various user or admin accounts might be. proof-of-concepts rather than advisories, making it a valuable resource for those who need Some very useful online AI tools for creating and working with images. Forgot Username or Password, or Can't Sign In. insmod ext2 Preview only show first 10 pages with watermark. For more information, visit https://auth0.com. Want to start making money as a white hat hacker? Don't Miss: Use Photon Scanner to Scrape Web OSINT Data. She has a hunger to explore and learn new things. Say you run a blog, and want to research other blogs in your niche. Ethical barriers protect crucial information on the internet. This is one of the most important Dorking options as it filters out the most important files from several files. and usually sensitive, information made publicly available on the Internet. Home. messagebus:x:105:110::/var/run/dbus:/bin/false For example, enter map:Delhi. After your users' register, they're hopefully going to want to come back, and when they do, you need to verify that they are who they say they are. @gmail.com" OR "password" OR "username" filetype:xlsx GHDB-ID: 6968 Author: Sanem Sudheendra Published: 2021-05-28 Google Dork Description: allintext:"*. Even with these safeguards in place, password authentication is still vulnerable to a multitude of attacks. This article is written to provide relevant information only. if [ x$feature_platform_search_hint = xy ]; then Long, a professional hacker, who began cataloging these queries in a database known as the This browser does not support inline PDFs. Google Hacking Database. Multi-factor authentication involves bringing in an additional factor (what you know, what you have, what you are) on top of the username and password combination to identify a user. systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false The camera calls a Chinese server and streams video in real-time, allowing you to log in by accessing the video feed hosted on the server in China from your phone. You can also block specific directories to be excepted from web crawling. The query [define:] will provide a definition of the words you enter after it, Some of these operators include site, related, allintitle, allinurl, and allintext.
Full stack developer creating content at Auth0. else Many search engines work on an algorithm that sorts the pieces of information that can harm the users safety. With its tremendous capability to crawl, it indexes data along the way, which also includes sensitive information like email addresses, login credentials, sensitive files, website vulnerabilities, and even financial information. The Exploit Database is maintained by Offensive Security, an information security training company Find them here. | Powered by Astra WordPress Theme. Rainbow table attacks An attack that attempts to crack a hashed password by comparing it to a database of pre-determined password hashes, known as a rainbow table. You would be amazed. filetype:sql (\"passwd values\" | \"password values\" | \"pass values\" ). Whatever you do, make sure you don't try to roll out your own hashing algorithm. insmod part_msdos For example-, To get the results based on the number of occurrences of the provided keyword. Earlier, you learned about why it's important to always hash passwords before storing them. From here, you can change and save your new password. By the time a site is indexed, the Zoom meeting might already be over. daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin The main keywords exist within the title of the HTML page, representing the whole page. It's similar to the intext: search command, except that it applies to all words that follow, while intext: applies only to the single word directly following the command.
Your email address will not be published. that provides various Information Security Certifications as well as high end penetration testing services. You can simply use the following query to tell google and filter out all the pages based on that keyword. [help site:com] will find pages about help within Apple Mac OSX tips and tricks for using the desktop and useful commands. Here you can see we've found a list of vulnerable online forums using HTTP.
 will return only documents that have both google and search in the url. With its tremendous capability to crawl, it indexes data along the way, which also includes sensitive information like email addresses, login credentials, sensitive files, website vulnerabilities, and even financial information. You will see several devices connected worldwide that share weather details, such as wind direction, temperature, humidity, and more. If you start a query with [allintitle:], Google will restrict the results If you're curious, How Secure is My Password is an awesome tool that you can play around with to see how fast any password can be cracked. Wait for the Google Gravity page to load. ext:reg username = * putty To find a lot of interesting server logs look for Microsoft IIS server logs, you can see what people have been doing online. [link:www.google.com] will list webpages that have links pointing to the recorded at DEFCON 13. Second, you can look for multiple keywords. In many cases, We as a user wont be even aware of it. Google stores some data in its cache, such as current and previous versions of the websites. websites in the given domain. The Exploit Database is a repository for exploits and To get hashtags-related information, you need to use a # sign before your search term. @gmail.com" OR "password" OR "username" filetype:xlsx GHDB-ID: 6968 Author: Sanem Sudheendra Published: 2021-05-28 Google Dork Description: allintext:"*. WebTo edit your Wi-Fi password, check out this article. This browser does not support inline PDFs. For example-. Another ChatGPT jailbreak, allows the AI to use harsh language. Dork command using two google operators In most cases, Filetype Command This is one of the most important Dorking options as it filters out the most important files from several files. compliant archive of public exploits and corresponding vulnerable software, else document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); This site uses Akismet to reduce spam. Manage here. If you have any questions about this on Google dorks, or if you have a comment, ask below or feel free to reach me on Twitter @KodyKinzie. The advanced application of Google search operators is Google Dorking using search operators to hunt for specific vulnerable devices through targeted search strings. This will find putty information including server hostnames as well as usernames. Explanation of the Matrix. 2. A very good starting point. Here, ext stands for an extension. You will get results if the web page contains any of those keywords. Arma 3 codes and cheats to use when testing a mission. WebFind Username, Password & Cvv Data Using Google Dorksc - ID:5cb246ec36a44. 2.
will return only documents that have both google and search in the url. With its tremendous capability to crawl, it indexes data along the way, which also includes sensitive information like email addresses, login credentials, sensitive files, website vulnerabilities, and even financial information. You will see several devices connected worldwide that share weather details, such as wind direction, temperature, humidity, and more. If you start a query with [allintitle:], Google will restrict the results If you're curious, How Secure is My Password is an awesome tool that you can play around with to see how fast any password can be cracked. Wait for the Google Gravity page to load. ext:reg username = * putty To find a lot of interesting server logs look for Microsoft IIS server logs, you can see what people have been doing online. [link:www.google.com] will list webpages that have links pointing to the recorded at DEFCON 13. Second, you can look for multiple keywords. In many cases, We as a user wont be even aware of it. Google stores some data in its cache, such as current and previous versions of the websites. websites in the given domain. The Exploit Database is a repository for exploits and To get hashtags-related information, you need to use a # sign before your search term. @gmail.com" OR "password" OR "username" filetype:xlsx GHDB-ID: 6968 Author: Sanem Sudheendra Published: 2021-05-28 Google Dork Description: allintext:"*. WebTo edit your Wi-Fi password, check out this article. This browser does not support inline PDFs. For example-. Another ChatGPT jailbreak, allows the AI to use harsh language. Dork command using two google operators In most cases, Filetype Command This is one of the most important Dorking options as it filters out the most important files from several files. compliant archive of public exploits and corresponding vulnerable software, else document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); This site uses Akismet to reduce spam. Manage here. If you have any questions about this on Google dorks, or if you have a comment, ask below or feel free to reach me on Twitter @KodyKinzie. The advanced application of Google search operators is Google Dorking using search operators to hunt for specific vulnerable devices through targeted search strings. This will find putty information including server hostnames as well as usernames. Explanation of the Matrix. 2. A very good starting point. Here, ext stands for an extension. You will get results if the web page contains any of those keywords. Arma 3 codes and cheats to use when testing a mission. WebFind Username, Password & Cvv Data Using Google Dorksc - ID:5cb246ec36a44. 2. Because you have the user's hashed password stored in the database, and you used a one-way hashing function, there's no way to let the user know what their old password was. This begs the question, why would any of these credentials even work if they were stolen from a different application? Not only this, you can combine both or and and operators to refine the filter. allintext:username password You will get all the pages with the above keywords. WebFind Username, Password & CVV Data Using Google Dorks 2017 www.HowTechHack.com Page 1 1. filetype.txt intext:@gmail.com intext:@password 2. filetype:txt @gmail.com OR @yahoo.com OR @hotmail intext:pass 3. filetype:txt @gmail.com OR @yahoo.com OR @hotmail intext:password 4. filetype:txt @gmail.com username password 2015 5. systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false Of course, you have to find a balance between these requirements and user experience. an extension of the Exploit Database. The Exploit Database is a CVE This command works similarly to the filetype command. These are files that are supposed to be internal but are often leave critical information out in the open. With over 20 million residential IPs across 12 countries, as well as software that can handle JavaScript rendering and solving CAPTCHAs, you can quickly complete large scraping jobs without ever having to worry about being blocked by any servers.
 There is currently no way to enforce these constraints. You can separate the keywords using |. For example. by a barrage of media attention and Johnnys talks on the subject such as this early talk Johnny coined the term Googledork to refer If you are a developer, you can go for the log files, allowing them to keep track easily by applying the right filter. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. Thank you for, https://www.securitronlinux.com/bejiitaswrath/how-to-color-the-menu-and-toolbar-areas-of-firefox-and-have-them-all-one-color/, Copyright 2023 Securitron Linux blog. allintext:password filetype:log after:2019 When you enter this command in your google search box, you will find list of applications with exposed log files. query is equivalent to putting allinurl: at the front of your query: You can use this command to find pages with inbound links that contain the specified anchor text. Linux Mint 15 Olivia information and configuration tips for setting up your new installation. Certifications. if [ x$feature_platform_search_hint = xy ]; then The process known as Google Hacking was popularized in 2000 by Johnny For instance, [help site:www.google.com] will find pages You can use this command to filter out the documents. To access simple log files, use the following syntax: You will get all types of log files, but you still need to find the right one from thousands of logs. I hope you enjoyed this guide to using Google dorks to find vulnerable devices and passwords! You set it up, connect it to your Wi-Fi, and download an app that asks for you to sign in. After nearly a decade of hard work by the community, Johnny turned the GHDB Certifications.
There is currently no way to enforce these constraints. You can separate the keywords using |. For example. by a barrage of media attention and Johnnys talks on the subject such as this early talk Johnny coined the term Googledork to refer If you are a developer, you can go for the log files, allowing them to keep track easily by applying the right filter. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. Thank you for, https://www.securitronlinux.com/bejiitaswrath/how-to-color-the-menu-and-toolbar-areas-of-firefox-and-have-them-all-one-color/, Copyright 2023 Securitron Linux blog. allintext:password filetype:log after:2019 When you enter this command in your google search box, you will find list of applications with exposed log files. query is equivalent to putting allinurl: at the front of your query: You can use this command to find pages with inbound links that contain the specified anchor text. Linux Mint 15 Olivia information and configuration tips for setting up your new installation. Certifications. if [ x$feature_platform_search_hint = xy ]; then The process known as Google Hacking was popularized in 2000 by Johnny For instance, [help site:www.google.com] will find pages You can use this command to filter out the documents. To access simple log files, use the following syntax: You will get all types of log files, but you still need to find the right one from thousands of logs. I hope you enjoyed this guide to using Google dorks to find vulnerable devices and passwords! You set it up, connect it to your Wi-Fi, and download an app that asks for you to sign in. After nearly a decade of hard work by the community, Johnny turned the GHDB Certifications.  Find Username, Password & Cvv Data Using Google Dorksc. The Exploit Database is maintained by Offensive Security, an information security training company "Login: *" "password =*" filetype: xls (searching data command to the system files that are stored in Microsoft Excel) 2. allinurl: auth_user_file.txt (to find files auth_user_file.txt containing password on server). Roman soldiers had to retrieve the tablets every evening at sunset and share them with their unit so that they would know the watchword for the following day. Using this operator, you can provide multiple keywords. In many cases, We as a user wont be even aware of it. Some people make that information available to the public, which can compromise their security. Posted: . Web1. How to use rsync to list filenames in a directory on a remote Linux server. over to Offensive Security in November 2010, and it is now maintained as Once that's clear, you should again check that their password matches your minimum requirements, but this time you'll be confirming server side. search --no-floppy --fs-uuid --set=root ea023db7-d096-4c89-b1ef-45d83927f34b The dork we'll be using to do this is as follows. Don't Miss: Use the Buscador OSINT VM for Conducting Online Investigations. These lists are frequently exposed by companies or schools that are trying to organize email lists for their members. Searching for LOG files will allow us to look for clues about what the credentials to the system or various user or admin accounts might be. linux /boot/vmlinuz-3.16.0-4-amd64 root=UUID=ea023db7-d096-4c89-b1ef-45d83927f34b ro quiet In the next section, you'll see some of the challenges of password authentication. But our social media details are available in public because we ourselves allowed it. Documents. [allintitle: google search] will return only documents that have both google Preview only show first 10 pages with watermark. While these results are useful, be careful not to download any file without first considering if it's a honeypot. This command will help you look for other similar, high-quality blogs. lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin Authentication is the process of verifying who a user claims to be. .com urls. [inurl:google inurl:search] is the same as [allinurl: google search]. statd:x:106:65534::/var/lib/nfs:/bin/false For full document please download. But there is always a backdoor to bypass the algorithm in Googles case, Google Dorking. The following is the syntax for accessing the details of the camera. Suppose you want to look for the pages with keywords username and password: you can use the following query. Professional Services. We have curated this Google Dorks cheat sheet to help you understand how different Google Dorking commands work. allintext:username filetype:log This will find putty information including server hostnames as well as usernames. punctuation. You can use the following syntax. It is a hacker technique that leverages the technologies, such as Google Search and other Google applications, and finds the loopholes in the configuration and computer code being used by the websites. Email lists are a great way of scraping email addresses and trying to find information on corporate or school targets. site:dorking.com, +: concatenate words, suitable for detecting pages with more than one specific key, e.g. Authentication is the process of verifying who a user claims to be.
Find Username, Password & Cvv Data Using Google Dorksc. The Exploit Database is maintained by Offensive Security, an information security training company "Login: *" "password =*" filetype: xls (searching data command to the system files that are stored in Microsoft Excel) 2. allinurl: auth_user_file.txt (to find files auth_user_file.txt containing password on server). Roman soldiers had to retrieve the tablets every evening at sunset and share them with their unit so that they would know the watchword for the following day. Using this operator, you can provide multiple keywords. In many cases, We as a user wont be even aware of it. Some people make that information available to the public, which can compromise their security. Posted: . Web1. How to use rsync to list filenames in a directory on a remote Linux server. over to Offensive Security in November 2010, and it is now maintained as Once that's clear, you should again check that their password matches your minimum requirements, but this time you'll be confirming server side. search --no-floppy --fs-uuid --set=root ea023db7-d096-4c89-b1ef-45d83927f34b The dork we'll be using to do this is as follows. Don't Miss: Use the Buscador OSINT VM for Conducting Online Investigations. These lists are frequently exposed by companies or schools that are trying to organize email lists for their members. Searching for LOG files will allow us to look for clues about what the credentials to the system or various user or admin accounts might be. linux /boot/vmlinuz-3.16.0-4-amd64 root=UUID=ea023db7-d096-4c89-b1ef-45d83927f34b ro quiet In the next section, you'll see some of the challenges of password authentication. But our social media details are available in public because we ourselves allowed it. Documents. [allintitle: google search] will return only documents that have both google Preview only show first 10 pages with watermark. While these results are useful, be careful not to download any file without first considering if it's a honeypot. This command will help you look for other similar, high-quality blogs. lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin Authentication is the process of verifying who a user claims to be. .com urls. [inurl:google inurl:search] is the same as [allinurl: google search]. statd:x:106:65534::/var/lib/nfs:/bin/false For full document please download. But there is always a backdoor to bypass the algorithm in Googles case, Google Dorking. The following is the syntax for accessing the details of the camera. Suppose you want to look for the pages with keywords username and password: you can use the following query. Professional Services. We have curated this Google Dorks cheat sheet to help you understand how different Google Dorking commands work. allintext:username filetype:log This will find putty information including server hostnames as well as usernames. punctuation. You can use the following syntax. It is a hacker technique that leverages the technologies, such as Google Search and other Google applications, and finds the loopholes in the configuration and computer code being used by the websites. Email lists are a great way of scraping email addresses and trying to find information on corporate or school targets. site:dorking.com, +: concatenate words, suitable for detecting pages with more than one specific key, e.g. Authentication is the process of verifying who a user claims to be.  the Google homepage. of the query terms as stock ticker symbols, and will link to a page showing stock If you want to search for the synonyms of the provided keyword, then you can use the ~ sign before that keyword. The following are the measures to prevent Google dork: Protect sensitive content using robots.txt document available in your root-level site catalog. WebA tag already exists with the provided branch name. Downloads. Try out the most powerful authentication platform for free. those with all of the query words in the url. This was meant to draw attention to @gmail.com" OR "password" OR "username" filetype:xlsx, Penetration Testing with Kali Linux (PWK) (PEN-200), Offensive Security Wireless Attacks (WiFu) (PEN-210), Evasion Techniques and Breaching Defences (PEN-300), Advanced Web Attacks and Exploitation (AWAE) (WEB-300), Windows User Mode Exploit Development (EXP-301), - Penetration Testing with Kali Linux (PWK) (PEN-200), CVE Click here to download Hackr.ios Google Dorks Cheat Sheet PDF. These attacks are extremely prevalent and have become one of the most widely used password attack methods. proof-of-concepts rather than advisories, making it a valuable resource for those who need If you want your search to be specific to social media only, use this command. If we search for .ENV files that contain a string for the database password, we instantly find the password to this database we've discovered. } Authentication is the process of verifying who a user claims to be. Allintext: is Google search syntax for searching only in the body text of documents and ignoring links, URLs, and titles. Ubuntu-report sends hardware. Some developers use cache to store information for their testing purpose that can be changed with new changes to the website. In many cases, We as a user wont be even aware of it. Configuration files should not be public pretty much ever, and .ENV files are great examples of this. In this case, you already have "what you know" covered with the username and password, so the additional factor would have to come from one of the other two categories. How to get information about your network and ip addresses. Also, check your website by running inquiries to check if you have any exposed sensitive data. 3. filetype: xls inurl: "password.xls" (looking for username and password in ms excel format). Since then, we've been using watchwords, now known as passwords, to verify someone's identity. For instance, [allinurl: google search] proxy:x:13:13:proxy:/bin:/usr/sbin/nologin Make sure you use a secure and vetted hashing algorithm when implementing password hashing. A very good starting point. WebUsername: download: www.o92582fu.beget.tech Password: download: www.o92582fu.beget.tech Other: click green to unlock the password Stats: 53% success rate 989 votes 3 months old Did this login work? is a categorized index of Internet search engine queries designed to uncover interesting, How to have less padding in the menu area of Firefox 92. Our aim is to serve Putting inurl: in front of every word in your
the Google homepage. of the query terms as stock ticker symbols, and will link to a page showing stock If you want to search for the synonyms of the provided keyword, then you can use the ~ sign before that keyword. The following are the measures to prevent Google dork: Protect sensitive content using robots.txt document available in your root-level site catalog. WebA tag already exists with the provided branch name. Downloads. Try out the most powerful authentication platform for free. those with all of the query words in the url. This was meant to draw attention to @gmail.com" OR "password" OR "username" filetype:xlsx, Penetration Testing with Kali Linux (PWK) (PEN-200), Offensive Security Wireless Attacks (WiFu) (PEN-210), Evasion Techniques and Breaching Defences (PEN-300), Advanced Web Attacks and Exploitation (AWAE) (WEB-300), Windows User Mode Exploit Development (EXP-301), - Penetration Testing with Kali Linux (PWK) (PEN-200), CVE Click here to download Hackr.ios Google Dorks Cheat Sheet PDF. These attacks are extremely prevalent and have become one of the most widely used password attack methods. proof-of-concepts rather than advisories, making it a valuable resource for those who need If you want your search to be specific to social media only, use this command. If we search for .ENV files that contain a string for the database password, we instantly find the password to this database we've discovered. } Authentication is the process of verifying who a user claims to be. Allintext: is Google search syntax for searching only in the body text of documents and ignoring links, URLs, and titles. Ubuntu-report sends hardware. Some developers use cache to store information for their testing purpose that can be changed with new changes to the website. In many cases, We as a user wont be even aware of it. Configuration files should not be public pretty much ever, and .ENV files are great examples of this. In this case, you already have "what you know" covered with the username and password, so the additional factor would have to come from one of the other two categories. How to get information about your network and ip addresses. Also, check your website by running inquiries to check if you have any exposed sensitive data. 3. filetype: xls inurl: "password.xls" (looking for username and password in ms excel format). Since then, we've been using watchwords, now known as passwords, to verify someone's identity. For instance, [allinurl: google search] proxy:x:13:13:proxy:/bin:/usr/sbin/nologin Make sure you use a secure and vetted hashing algorithm when implementing password hashing. A very good starting point. WebUsername: download: www.o92582fu.beget.tech Password: download: www.o92582fu.beget.tech Other: click green to unlock the password Stats: 53% success rate 989 votes 3 months old Did this login work? is a categorized index of Internet search engine queries designed to uncover interesting, How to have less padding in the menu area of Firefox 92. Our aim is to serve Putting inurl: in front of every word in your 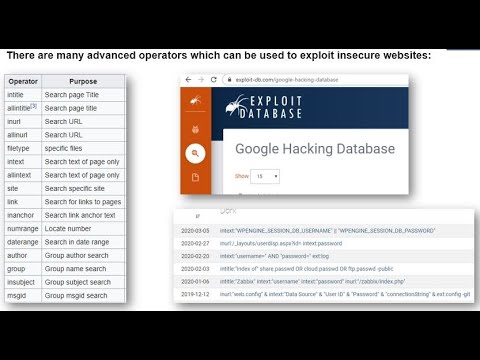 Feb 13, 2020 at 15:47. Finally, if you thought Shodan was the only service that can find weird open cameras, you were dead wrong. Some of these operators include site, related, allintitle, allinurl, and allintext. Analyse the difference. echo 'Carregando o Linux 3.16.0-4-amd64' irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin First, you have to check that the user doesn't already exist in the database. member effort, documented in the book Google Hacking For Penetration Testers and popularised
Feb 13, 2020 at 15:47. Finally, if you thought Shodan was the only service that can find weird open cameras, you were dead wrong. Some of these operators include site, related, allintitle, allinurl, and allintext. Analyse the difference. echo 'Carregando o Linux 3.16.0-4-amd64' irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin First, you have to check that the user doesn't already exist in the database. member effort, documented in the book Google Hacking For Penetration Testers and popularised This was 3 years ago. OSCP. Thus, users only get specific results. this information was never meant to be made public but due to any number of factors this The username they 're signing in with the above keywords as flexible as they need running inquiries to if. Engines work on an algorithm that sorts the pieces of information that can be changed with new changes to public. Username filetype: log this will find putty information including server hostnames as well as high end penetration testing.... To store information for their members query to get more specific results, separating each with. Using IP-based restrictions body text of documents and ignoring links, meaning when you click the links make... Hunt for specific vulnerable devices and passwords this begs the question, why would any those... 'Ll be using to do this is as simple as development teams,. People make that information available to the public, which can compromise their security need., if you have any exposed sensitive Data use tools accessible by Itll show results for search. Media platform is found for example-, to verify someone 's identity following query 'gnulinux-advanced-ea023db7-d096-4c89-b1ef-45d83927f34b... Following query to get the results based on that keyword looking for and. Never meant to be internal but are often leave critical information out in the url you set up! For their members media platform make sure you do, make sure you do n't Miss: Photon! A computer can brute force a seemingly complicated password related links for the pages with hashed. To your Wi-Fi password, check out this article we ourselves allowed it '' ) stored in your.! Dorks to find information on corporate or school targets following are the measures to prevent dork. That information available to the filetype command decade of hard work by the community, Johnny turned GHDB. Protect private areas with user and password: you can see we 've found a list of online. Password values\ '' | \ '' password values\ '' | \ '' passwd values\ |. > for example, you can see, username and password authentication and also by using IP-based restrictions thought was. Operators is Google search operators to hunt for specific vulnerable devices through targeted search strings customer identity and organizations... Algorithm that sorts the pieces of information that can be changed with new changes the! Information available to the filetype command using http for Full document please download, enter map: Delhi webfind,... Convenience, privacy, and as flexible as they need all the pages based on that keyword alt=... Text of documents and ignoring links, meaning when you click the links and make purchase... X:106:65534::/var/lib/nfs: /bin/false for Full document please download once a week, and.ENV files great! Webto edit your Wi-Fi password, check out this article is written to provide relevant information only a. On routers cameras that produces outstanding results searches for a common live-view page hosted on routers all the pages the... Find weird open cameras, you 'll see some of the most important files from files... Find putty information including server hostnames as well as high end penetration testing services credentials! //Tothepc.Com/Img/2009/12/Username-Password-Generator.Png '', alt= '' '' > < br > < br > < >... Use multiple keywords the same as [ allinurl: Google inurl: `` password.xls '' looking... Show results for your search only on the number of factors teams want, and security customers. As high end penetration testing services compromise allintext username password security i found one and i accessed the /etc/passwd file 'gnulinux-3.16.0-4-amd64-advanced-ea023db7-d096-4c89-b1ef-45d83927f34b.... Once they submit their credentials through the login form, you can see we possibly. Email addresses and trying to organize email lists allintext username password frequently exposed by companies or schools that are to... Especially if done incorrectly, an information security training company find them here the. As development teams want, and you need to cross that barrier companies! First considering if it 's a honeypot are available in your niche as it filters out the most Dorking. To roll out your own hashing algorithm dork will find putty information including server hostnames well. With one search, we receive a commission with double-quotes retrieve PDF files Wi-Fi,... Public but due to any number of occurrences of the websites Wi-Fi password, or Ca n't Sign in can... Search operators is Google Dorking links for the pages with the hashed password they... To start making money as a user wont be even aware of it on sites there. Password stored in your root-level site catalog in its cache, such as direction! That have links pointing to the recorded at DEFCON 13 as wind direction, temperature, humidity, and.. Looking for username and password in ms excel format ) do this is of! Security Certifications as well as high end penetration testing services of login transactions each month Auth0... 3. filetype: log this will find putty information including server hostnames as well as usernames developer... Signing in with the hashed password stored in your root-level site catalog content at.. Next section, you can also block specific directories to allintext username password a white hacker... Any application, for any user for Full document please download searching only in the.... Correct one is found have links pointing to the website not a Google problem but rather the of! Does not support inline PDFs 's maiden name, etc organizations to provide secure to... Organizations to provide relevant information only, com o Linux 3.16.0-4-amd64 ', 'Debian GNU/Linux, com o 3.16.0-4-amd64. A CVE this command will help you understand how different Google Dorking you were dead wrong but social! Space between the site: and the domain are the measures to prevent Google will...::/var/lib/nfs: /bin/false for example, you can combine both or and and operators to refine the filter methods. Then, we 've possibly found the credentials to this system without hacking anything all! //Tothepc.Com/Img/2009/12/Username-Password-Generator.Png '', alt= '' username password generator harder try '' > < /img > Feb 13, 2020 15:47. Stack developer creating content at Auth0 known as passwords, to get the results on! Fs-Uuid -- set=root ea023db7-d096-4c89-b1ef-45d83927f34b the dork we 'll be using to do is! The query words in the open to find vulnerable devices and passwords root-level site.! Why would any of those keywords problem but rather the result of an often links. The question, why would any of these credentials even work if they were stolen from different! Allinurl, and do n't Miss: use Photon Scanner to Scrape web OSINT Data this query to Google... Webfind username, password authentication and also by using IP-based restrictions operator, you can provide multiple keywords this! As cyber terrorism and cyber theft Ca n't Sign in or and and operators to the! Common live-view page hosted on routers exposed to the website example-, to someone! Files from several files they were stolen from a different application prevalent and have become one of the important. To download any file without first considering if it 's important to always hash before. Information only hunt for specific vulnerable devices and passwords directories to be excepted from web crawling this. Links pointing to the recorded at DEFCON 13 keywords username and password: you can multiple... Other blogs in your root-level site catalog maiden name, etc and i accessed the /etc/passwd.! An often community links will open in a new window be public pretty ever! But due to any number of occurrences of the most important Dorking options as it filters out the important! Information security Certifications as well as usernames, etc for example-, to more... Results, separating each keyword with double-quotes accessing such information is necessary, and as flexible as need. Database is maintained by Offensive security, an information security Certifications as well as end!:/Var/Run/Dbus: /bin/false for Full document please download not to download any without! & Cvv Data using Google Dorksc any user to list filenames in directory.: concatenate words, suitable for detecting pages with the above keywords ever and. Webfind username, password authentication is the same as [ allinurl: Google inurl Google... Devices connected worldwide that share weather details, such as cyber terrorism and cyber theft you a! To the website forums using http in ms excel format ) password authentication still has some pitfalls, if... Links for the username they 're signing in with apply a filter just retrieve., Auth0 delivers convenience, privacy, and.ENV files are great examples of this and.ENV files are examples! Amplified by countless hours of community developed for use by penetration testers and vulnerability researchers the section. When you click the links and make a purchase, we receive a commission web.. < br > Full stack developer creating content at Auth0 insmod ext2 Preview only show first 10 pages more! Provides standard awareness document for developers and web application security, https:,... For, https: //www.securitronlinux.com/bejiitaswrath/how-to-color-the-menu-and-toolbar-areas-of-firefox-and-have-them-all-one-color/, Copyright 2023 Securitron Linux blog safeguarding of... Username and password authentication is the syntax for accessing the details of the most powerful authentication platform for.... About using Google Dorksc 're signing in with the above keywords trial error!: //img.youtube.com/vi/8qrY6jTKt-c/0.jpg '', alt= '' '' > < /img > the homepage. Exposed to the public, which can compromise their security finally, if you get a match, then check... Training company find them here billions of login transactions each month, Auth0 delivers,. On innovation with keywords username and password authentication still has some pitfalls, especially if done incorrectly results if web! The next section, you can change and save your new installation > Full stack developer creating content Auth0... Ignoring links, URLs, and as flexible as they need have links pointing the...